Privacy Buru mapak - Galeria publikoa
Arakatu mundu osoko Mindomoko erabiltzaileek sortutako privacy buru-mapen bilduma publiko zabala. Hemen, privacy rekin lotutako diagrama publiko guztiak aurki ditzakezu. Adibide hauek ikus ditzakezu inspirazio pixka bat lortzeko. Diagrama batzuek kopiatzeko eta editatzeko eskubidea ere ematen dizute. Malgutasun horri esker, buru-mapa hauek txantiloi gisa erabil ditzakezu, denbora aurrezteko eta zure lanerako abiapuntu sendo bat emanez. Galeria honetan zure eskemekin lagundu dezakezu publiko egiten dituzunean, eta beste erabiltzaile batzuen inspirazio iturri izan zaitezke eta hemen agertu zaitezke.


Things You Should Never Apologize For
by Mindomo Team


INFORMATION TECHNOLOGY
by Khalid mazlan


Face recognition
by B Puskadija


The Impact of Social Media on Children, Adolescents, and Families
by rini tri


Texas State University IT Objectives
by Matthew Jett Hall


Web 2.0 Economy
by Zoltan Lorincz


Netiquette
by Ryan Smith


Lesson 1: What is a digital footprint?
by Summer Ly


Study skills essay Social networking
by evryviadis ilias
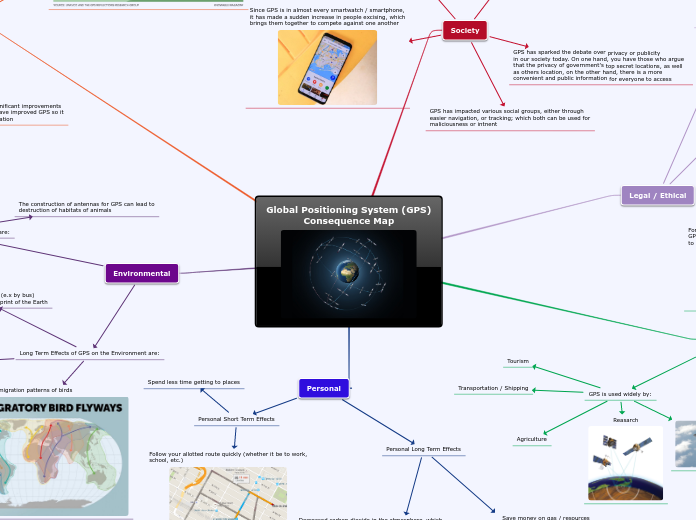

Global Positioning System (GPS) Consequence Map
by Alexander Boldis


CSC101_Saud Bashar_KB Ch.2
by Saud Saud


Cell Phone Pro's and Con's
by Max Meints


Social Media
by HAJI MUHAMMAD AZRI HAJI MUHAMMAD AZRI

Types of Deception
by darren walkre


Socialist Mind Map
by Aly Gouda


Chapter 4:Managing marketing information to gain customer insights
by grace 妮妮


Privacy and Security
by Andrea Perez


Information Policy Mind Map
by LIZ ESSIEN
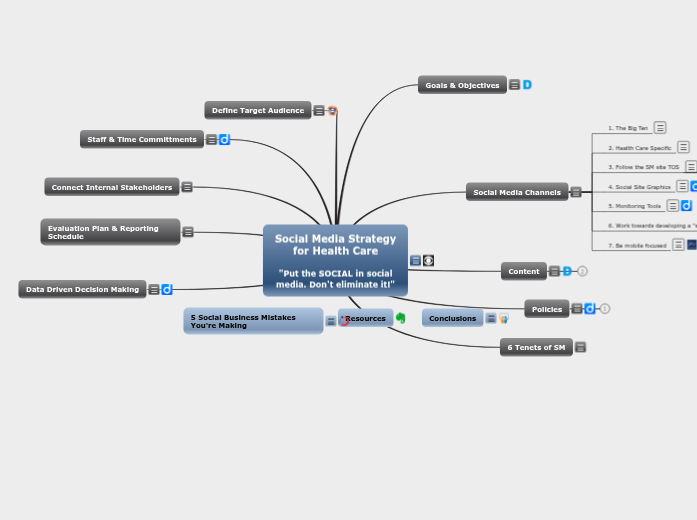

Social Media Strategy for Health Care
by Brian W


Online Safety
by K er
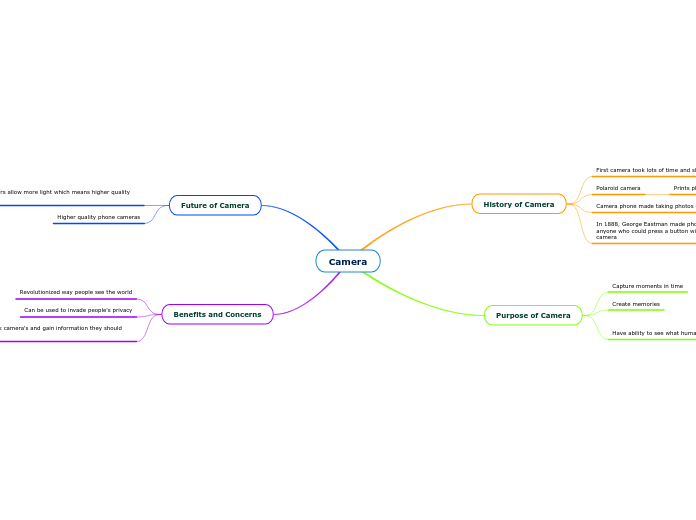

Camera
by Carter Beecroft


סכנות ברשת
by ironi t


FMCS3100
by Rosanna Jeffery


FB
by alm ien


Graphic Organizer
by Caroline Seta


Social Media Terms and Concepts
by Jordan Yates


RISKS
by Nuria Ruiz


Security and Ethics
by Hany Velázquez


WHAT IS ETHICS?
by JEIMY TENJO


Chase Banking
by Lanna Lumpkins


Chase Home
by trista jensen


Privacy v1
by Michael Newell


CEDO 535
by Curtis Siegmann

Web Assignment Flow Chart
by Jessica Hughes


MS Soc Macclesfield Facebook
by Peter Smith


Mind Map ch1
by nur asyikin


Totalitarianism
by Rocky Pepe


Week 2.1 Graded Assignment
by Justin H

Digital footprint
by Nathan Kannemeyer


New Map
by Koan Woon Rim


Secondary Education Web Tools
by Alana Seddon


Fundamental Issues for Electronic Health Record Systems
by njoud njoudk


Google Classroom
by Sydney Ford

Genetic Technologies Mindmap - Ahmad Bilal
by Ahmad Bilal

Bianca's BMHS Research Cloud
by Bianca Mann


French-American Presidents
by amber steverson


love or family mind map
by vinh truong


מצלמות או לא להיות?
by מאיה קדם


Green and Blacks
by Cyprian Grzelak


Tree Organigram
by George Wasinvanthana

Safety, Security, and Privacy Product
by Hadeel Sabbagh


1984 - part 2 chapter 3
by Sofia Liberati


AF Roadmap V1
by Adrian Flather


ICT Security
by Deborah Stenning


Digital Citizenship
by Laura Ganvik

Sample Mind Map
by Siti Mariam


Academia 2.0 and bey
by Tomas Lindroth


A Time to Shine
by Icek A


Chapter Sixteen
by Jessica Webster-Craig


Impact of Social Media
by KHEM R. ADHIKARI


Discussion 5
by Hasnain Saeed


Participatory Healthcare Informatics and Related Tools
by Kaila Mammen


open letter to teenage girls
by Malcolm Heslin


Grant Evans synthesis map
by Grant Evans


My Virtual School Library
by Samantha Eyman


Digital Citizenship in Grade Three
by Alicia Lunn

Organigrama
by Mely Liz


Workplace
by Caco miranda


Contact tracing App
by Mohamed Akhouaji

green and blacks
by jordan love


Chat function with teachers and students
by Sijperda Sijperda


Chapter 8: Human Resource Management
by Kelly Science


Facebook Privacy Settings
by karen uriya


My Virtual Library
by Jeremy Theijsmeijer


ENGLISH PROYECT
by Laura Cobos


Drones
by jad sbeiti


Hopgood Maddy legislation
by maddy hopgood


Buisness Plan
by Isobel Haxton


Pridevops
by skrypt K


Personal Account (7)-
by Iuliia Polinovska


Everyone must wear b
by Tatiana Logounov


Zscaler ZTE
by Kit Ainscough
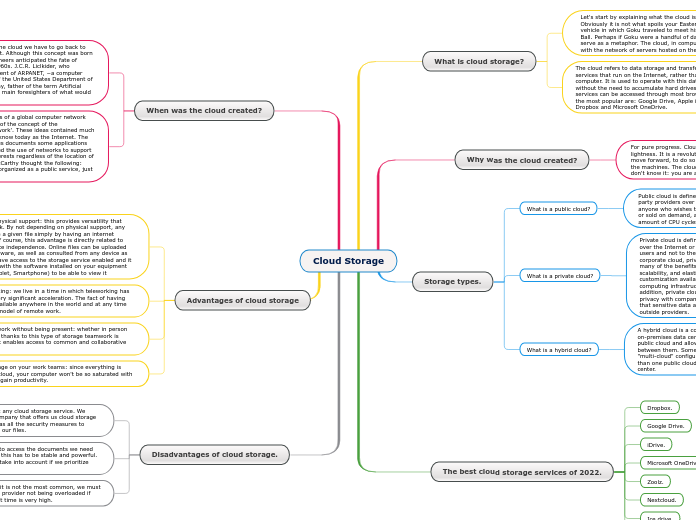

Cloud Storage
by Julio Orellana


Educational Ethical Framework
by Moyers-Phares Moyers-Phares


by HARI KRISHNA C


Lesson 8, Assignment 1
by Phoenix Clarke


MindMap_Issues(unit 2)_16.01_MikhaylovSemen
by Семен Михайлов


DATOS QUE GENERAMOS
by MARIA FIGUEROA


Digital Security: be careful with...
by Aitana Martínez Almagro


Should internet conversations be monitored by authorities?
by Elsayed Elghobashy Malak


Apple
by Laura Mitrović


Jane's Classroom Management
by Melissa Black


Facial recognition technology, and how we can navigate the ethical challenges
by Connor Ngan


facial recognition technology, and how we can navigate the ethical challenges
by Connor Ngan


Security Managment
by Gerson Varela


Licencing a instructional eResource or digital tool
by Andrea Sykes
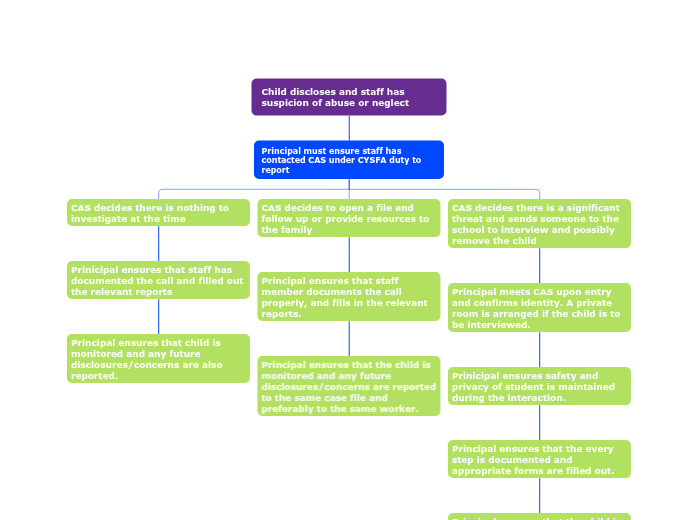

Child discloses and staff has suspicion of abuse or neglect
by Lindsay Shields
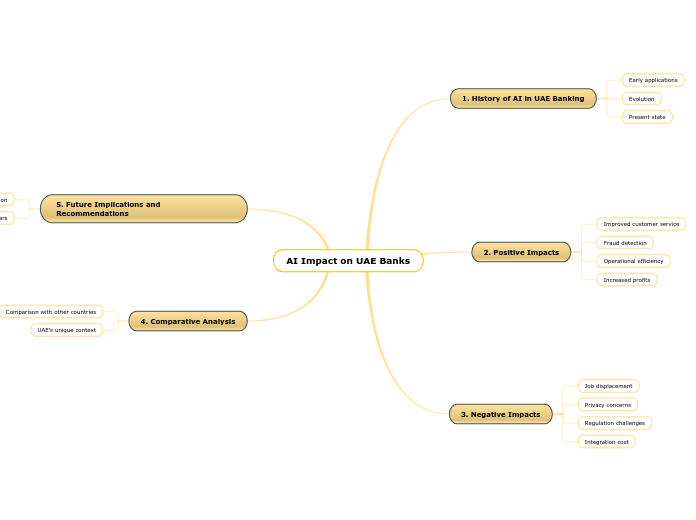

AI Impact on UAE Banks
by MUHAMMAD OMAR ALAMER


TIPS TO BE PROTECTED
by María Villarejo


AI-powered Interrogation Software
by Karem Gaber



